Waseda Frontline Research Vol. 18: Combating Unknown Threats and Hardware Trojans (Part 1 of 4)
Wed, Jan 17, 2018-
Tags
Nozomu Togawa, Professor, Faculty of Science and Engineering
Specialization: IoT, information and communications technology
Part 1: Using Artificial Intelligence to Detect Trojan Horses
 We are quickly reaching a point where the world will become flooded with the Internet of Things (IoT), making the world more convenient and prosperous. Despite such expectation, there are those with malicious intent, threatening such a world, and they have begun casting a shadow on this future of convenience. Professor Nozomu Togawa of the School of Fundamental Science and Engineering is studying how to use information and communications technology to quickly neutralize these risks to future society, and create safe and secure systems that are easy to use. This four part series will cover his research efforts and his thoughts on them. (Interview date: September 7, 2017)
We are quickly reaching a point where the world will become flooded with the Internet of Things (IoT), making the world more convenient and prosperous. Despite such expectation, there are those with malicious intent, threatening such a world, and they have begun casting a shadow on this future of convenience. Professor Nozomu Togawa of the School of Fundamental Science and Engineering is studying how to use information and communications technology to quickly neutralize these risks to future society, and create safe and secure systems that are easy to use. This four part series will cover his research efforts and his thoughts on them. (Interview date: September 7, 2017)
Security Measures in the IoT Age
I specialize in IoT/information and communications technology. One of my major research topics is establishing information security technologies, which is what I am working on at the moment. In my laboratory, we particularly focus on developing security technologies for equipment, devices, and other hardware that make up computer systems. Part of that is studying technology to detect hardware Trojans.

Professor Nozomu Togawa
People say that we are on the cusp of an age where not just conventional information and communications devices, such as smartphones and computers, but everything, including home electronics, automobiles, robots and facilities, will be connected together over a network. This concept, referred to as the Internet of Things (IoT), will play a central role in this new world. According to the 2016 White Paper on Information and Communications, a document released by the Ministry of Internal Affairs and Communications, there will be more than 30 billion IoT devices connected worldwide by 2020. As IoT continues to spread, information and communications security measures will become especially important. As more things connect over a network, this will increase the chances of fraud. IoT devices follow different standards, so it is extremely difficult to apply off-the-shelf security, increasing the risk of becoming victim to all kinds of external attacks.
Countering Trojan Horses
You have probably heard of Trojan horses in the context of information and communication. A Trojan horse is a type of malicious software that infects computer software. They are used for various fraudulent purposes, such as recording keystrokes from an infected computer and sending them over a network to the attacker. A hardware version of a Trojan horse is called a hardware Trojan. In other words, a hardware Trojan is a circuit that is illegally embedded in an integrated circuit (IC) and used to engage in some kind of fraudulent activity.
There have been many reports of cases throughout the world where damage may have been caused by these hardware Trojans. One example was a case where a malicious IC chip embedded in an electronic iron that was connected to the Internet was used to spread a large amount of unsolicited email. This was said to be the work of a hardware Trojan. Another example was a case where a major information and communications company acquired a computer manufacturer, where it was reported that fraudulent IC chips were embedded in the manufacturer’s computers, which were used to send data to destinations other than the intended recipient. Such a rumor can result in a sharp fall in share prices for the affected company or people stop using its products, suggesting that hardware Trojans are a significant risk to society.
Japan is also vulnerable to the threat of hardware Trojans. In fact, Japan is at great risk. Instead of producing semiconductors (a core component for hardware) in-house, many Japanese companies outsource the production of parts and circuits. Imagine a scenario where an ill-intentioned employee at a company supplying these parts embeds a fraudulent circuit in a part. Then, imagine that an encryption system used for security purposes is embedded in a part containing this circuit. When text is entered into this encryption system, it generates encrypted text. A user would think that the circuit is operating as expected. However, a hacker could design the circuit in such a way that a malicious program operates when provided with a certain input.

Photo: Professor Togawa giving a presentation on “Using Machine Learning to Detect Hardware Trojans”
The most popular encryption technology used today, known as RSA, uses 21,024 keys. It is extremely difficult using current technology to encrypt all patterns of plain text and to check whether text is properly encrypted. In general, a limited set of test patterns is run on completed circuits, and a circuit is deemed safe if there is a proper encryption output. However, not everything is tested, and a malicious circuit could very well be embedded in a part that otherwise looks fine.
Hardware Trojans are tiny parts embedded in circuits, and cannot be detected with the naked eye. On top of that, some parts in household IoT products now include embedded circuits that can be rewritten, making it easy for a malicious user to install a fraudulent program. This means that, in order to protect computers and IoT devices from hardware Trojans, we need a way to access the hardware itself.
Analyzing Fraudulent Circuits to Reveal Nine Types of Hardware Trojan Characteristics
We took on the challenge of developing technologies to detect hardware Trojans. First, we tried to find characteristics of circuits that make up hardware Trojans because understanding such characteristics would be of great help in detecting hardware Trojans.
There is a US-based website called Trust-HUB, which gathers information on actual hardware Trojan cases. I worked with graduate students in my laboratory to analyze fraudulent circuit diagrams covered on this website. We found that we could categorize its characteristics into nine types.
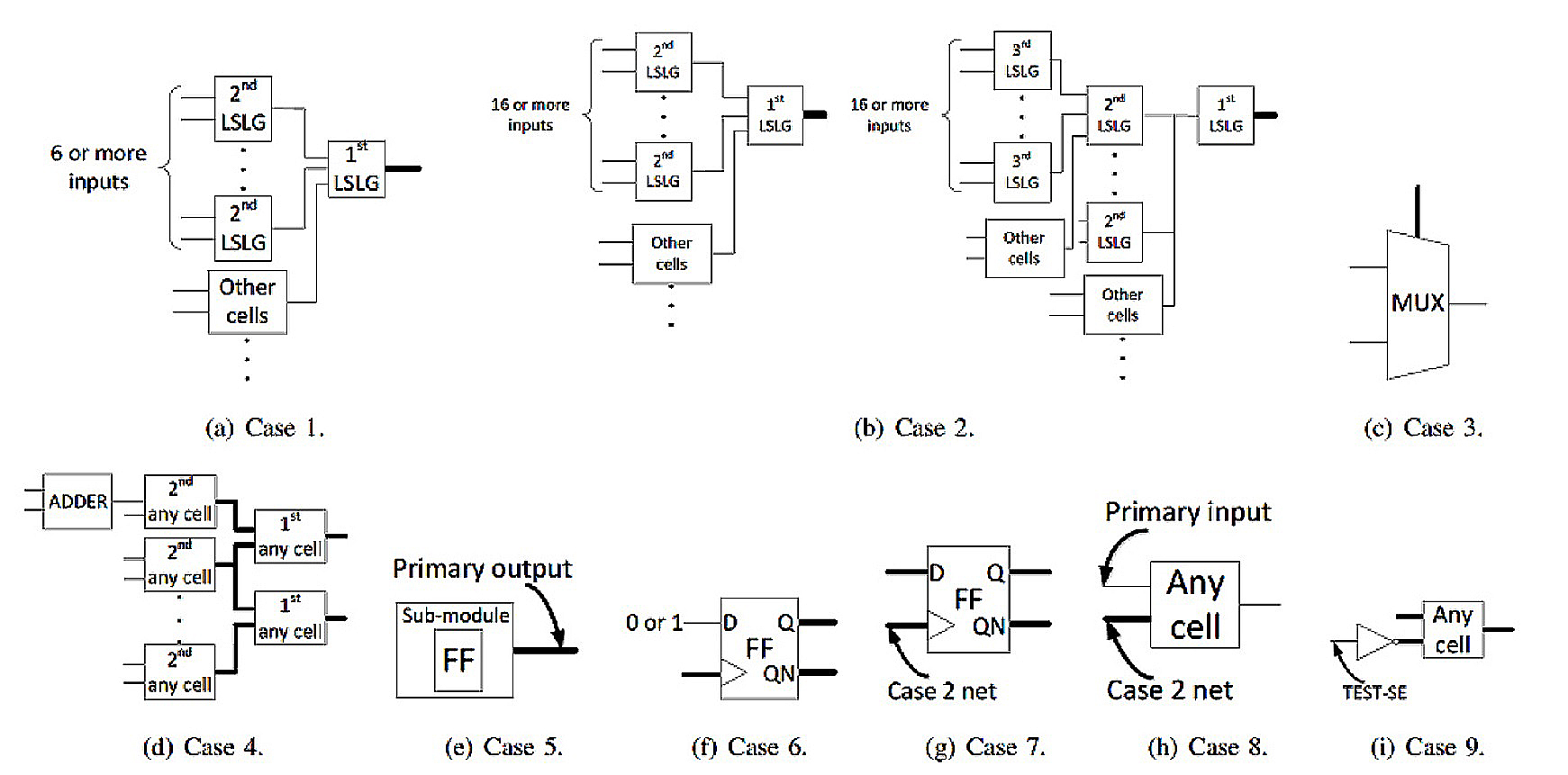
Figure: Nine types of characteristics found in circuits making up hardware Trojans were revealed after a detailed survey of Trust-HUB (Source: Togawa Laboratory)
Next, we assigned scores to circuits we wanted to check, such as one point for circuits that match characteristic #1 or two points for those that match characteristic #5 or #6. For example, a circuit that matched characteristics #1, #5, and #6 would have a total score of five points. We also discovered a basis for the ideal scoring to determine the existence of a real hardware Trojan.
We then introduced partial exception processing. This ultimately allowed us to build a system capable of determining whether a circuit actually contained a Trojan. We applied our detection method to check whether the model circuits listed on Trust-HUB contained hardware Trojans, and were able to detect every circuit without error. We believe we are the first in our field to develop technology to accurately detect hardware Trojans.
Using Artificial Intelligence to Combat Unknown Threats
We also decided we would need to handle unknown threats, so we then attempted to develop technology that would use artificial intelligence to detect unknown hardware Trojans. We are using machine learning, a core technology used for artificial intelligence, to try to accurately detect which wires in a circuit make up a hardware Trojan.
As mentioned previously, we had already identified nine types of hardware Trojan characteristics. Based on this information, we are using artificial intelligence to obtain characteristics to determine whether a circuit contains a hardware Trojan in the form of a quantity (characteristic quantity). Currently, we are developing technology to obtain characteristics to determine whether localized structures in circuits are hardware Trojans. We would like to develop technology capable of obtaining characteristic quantities by taking a larger view of circuits.
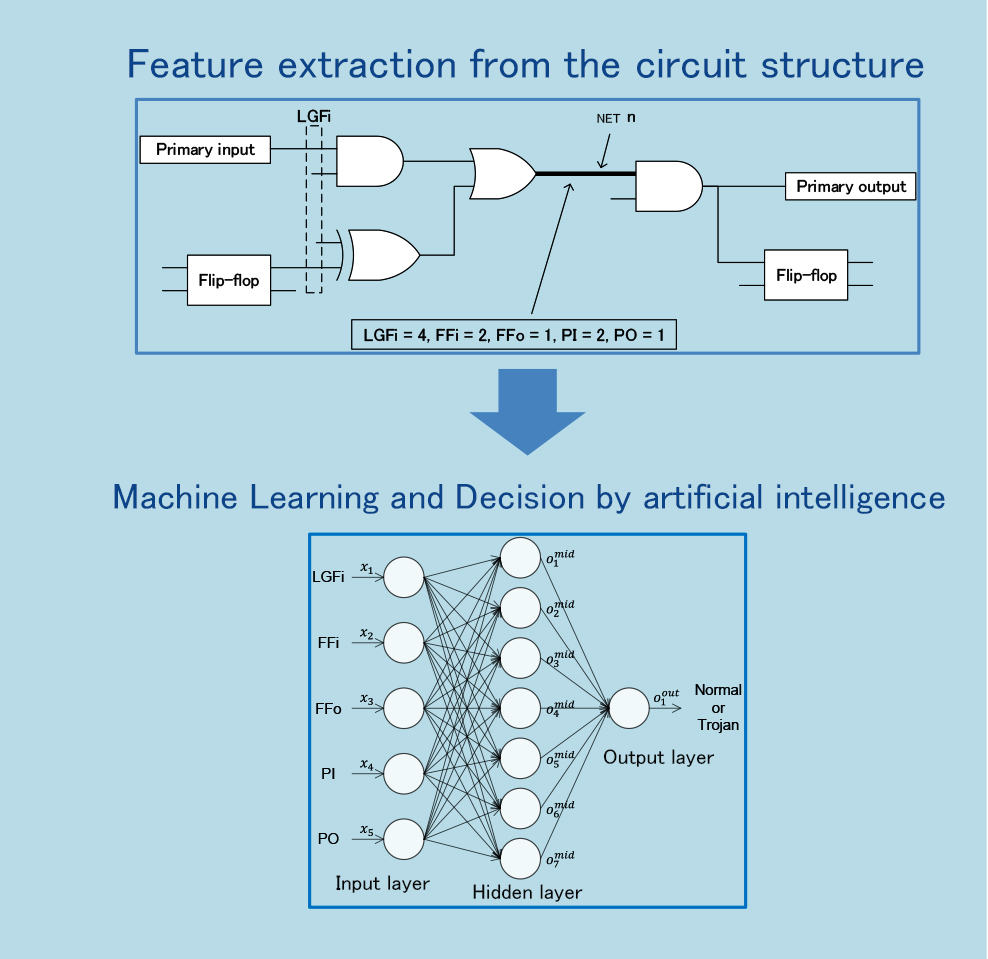
Figure: The process for using artificial intelligence to detect hardware Trojans. The goal is to detect unknown hardware Trojans without error (Source: Togawa Laboratory)
We are also figuring out ways to detect whether hardware Trojans might be embedded in IoT products by searched parts outside of the circuit. For example, all home electronics use electricity, so they consume power. If a product contains a hardware Trojan, the way it uses power should be abnormal. We are therefore considering ways to detect whether power is being consumed abnormally. One possible approach is to search for abnormalities in power consumption waveforms. Another method is to record statistics such as memory usage or CPU loads from outside the system to check for abnormalities that might suggest the existence of a hardware Trojan.
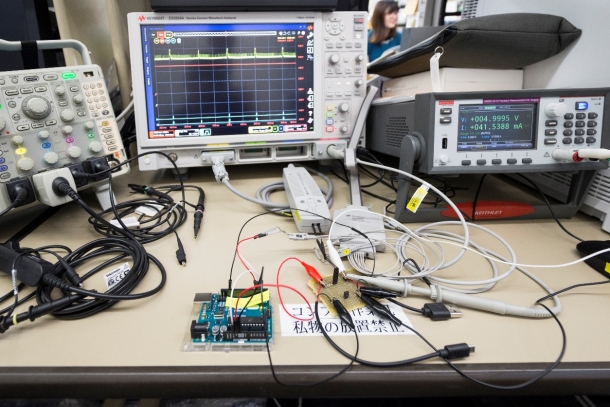
Photo: This method attempts to detect hardware Trojans by finding abnormalities in current waveforms. Five spikes can be seen in the current waveform (yellow line) on the monitor. Note how the second spike from the left has a different shape (thinner). This method attempts to detect fraudulent activity from such minor abnormalities.
Happy Ending for Everyone
How could hardware Trojan detection actually be used? The first application that comes to mind would be to install such a system in high cost IoT devices. One example might be a luxury connected car used by a VIP. Such a vehicle would require robust security measures. When discussing security, it is often said that ensuring security drives product prices up, which tends to hinder the distribution and development of such products. We believe that it is important for industry organizations and nations to collaborate with researchers like us to make sure that everyone is happy.
In Part 2, Professor Togawa will discuss geographical information processing systems.
☞Click here for Part 2
☞Click here for part 3
☞Click here for part 4
Profile
 Nozomu Togawa
Nozomu Togawa
Professor Togawa completed the Electrical Engineering Doctoral Course at the Waseda University Graduate School of Science and Engineering in 1997 (Doctor of Engineering). He has worked as a research associate in the School of Science and Engineering, Electronic/Information Communication Department, Waseda University; an assistant professor in the Faculty of Environmental Engineering, University of Kitakyushu; and an associate professor in the School of Fundamental Science and Engineering, Department of Computer Science and Engineering, Waseda University. Since 2009, he has worked as a professor in the Faculty of Science and Engineering (School of Fundamental Science and Engineering) at Waseda University. He specializes in integrated circuit design, and related applied technologies and security technologies. He has been the recipient of many awards, including The Telecommunications Advancement Foundation’s Telecom System Technology Award (2011). For details, visit the Togawa Laboratory
Major Achievements
Publications
- Hardware Trojans classification for gate-level netlists based on machine learning (2016 IEEE 22nd International Symposium on On-Line Testing and Robust System Design, 2016, p.203-206)
- A score-based classification method for identifying Hardware-Trojans at gate-level netlists (Design, Automation & Test in Europe Conference & Exhibition, 2015, p465-470)
- A Stayed Location Estimation Method for Sparse GPS Positioning Information (2017 IEEE 6th Global Conference on Consumer Electronics, 2017)
- An Accurate Indoor Positioning Algorithm using Particle Filter based on the Proximity of Bluetooth Beacons (2017 IEEE 6th Global Conference on Consumer Electronics, 2017)
Honors and Awards
1994 Student Paper Award, The Telecommuncations Advancement Foundation
1995 Best Paper Award, IEEE Asia and South Pacific Design Automation Conference
1995 Isao Okawa Memorial Achievement Award, Waseda University
1995 Azusa Ono Memorial Award, Waseda University
1996 Honorable Mention at the Circuit and Systems Workshop in Karuizawa, Nagano, JP, The Institute of Electronics, Information and Communication Engineers
1996 Ando Incentive Prize for the Study of Electronics, The Foundation of Ando Laboratory
1997 Yasujiro Niwa Outstanding Paper Award
2001 Takeda Techno-Entrepreneurship Award, The Takeda Foundation
2009 Honorable Mention from the Marubun Research Promotion Foundation
2009 Funai Academic Award, Funai Foundation for Information Technology
2010 Telecommunications System Technology Award, The Telecommunications Advancement Foundation














